
We all know that cyber-crime is increasing every year and at the moment we seem to be losing the battle against the blacks out there. Clearly the solution is to brick up the cyber walls and hope for the best ? But is that really the best approach?
In security circles, the mantra is defence in depth – and for many years this served us well.
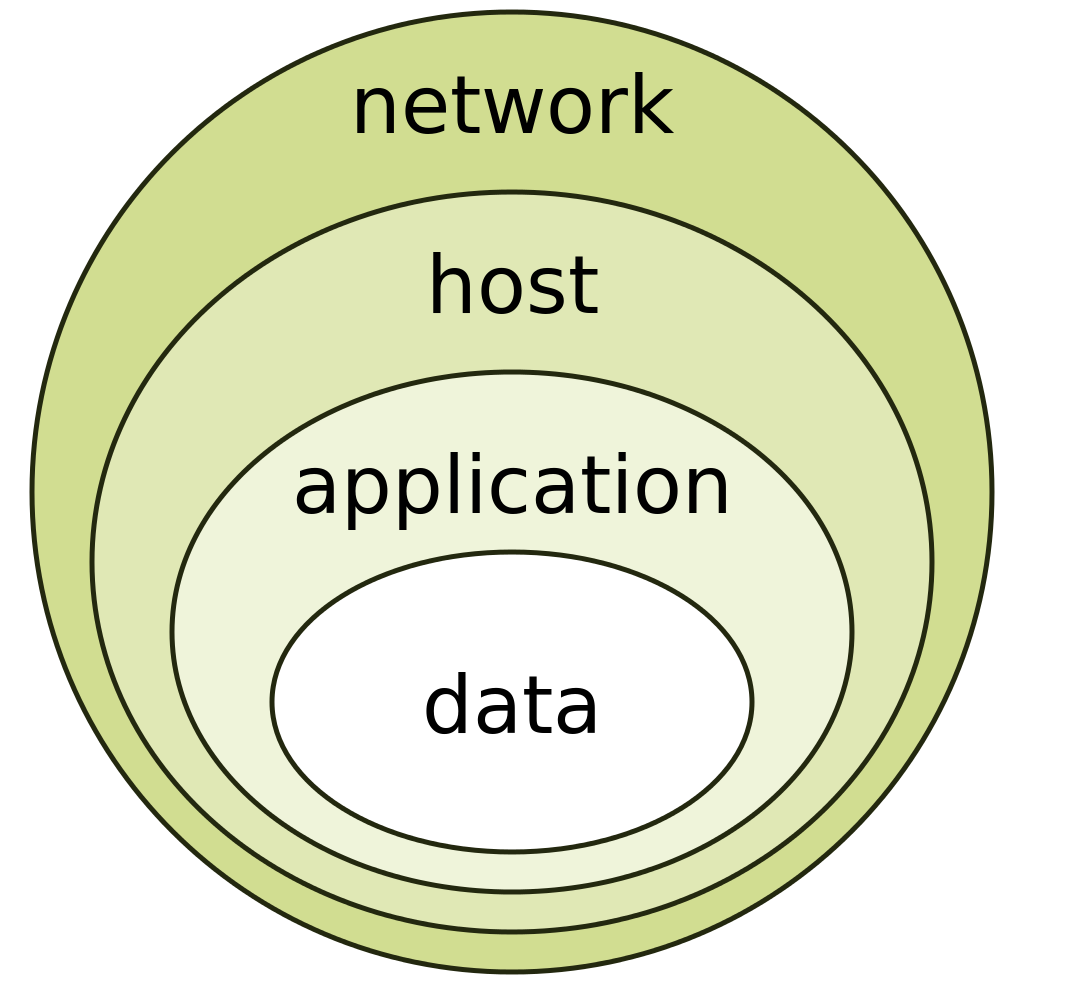
Organisations built strong firewalls and DMZs and stopped employees interacting with the internet. Emails were checked in and out of the organisation and ports were blocked, file-sharing and messaging sites were banned and blocked, and for a time that worked.
But times have changed. Employees of almost every type of organisation are quickly moving more and more of their work to mobile devices – whether mobile phones or tablets – and after a brief time when mobile devices were forced to use a VPN (this was quickly dropped by most companies dropped as a strategy as it was so cumbersome) we now live in a world where services are offered directly over the internet. The distinction between being “inside” and “outside” the company network are blurring – and in may companies today most employee systems are accessible without VPN.
A second trend is the switch from hacking events being primarily motivated by mischievousness or an intent to disrupt, to a more systematic focus on the theft of data. Hardly a day goes by without another company announcing that it has suffered a data breach with a huge variety of data being stolen and immediately sold to the highest bidder somewhere on the internet.
And, of course these trends are against a background of an overall threat increase – and the result is a substantial increase in reported data thefts.

This starts to bring into question some of the long-held approaches to security.
The defence in depth model gives the impression that if you sufficiently secure the perimeter and then the network and servers, then you are fairly safe, but this is not the case.
If we focus on perimeter security, then we are not focused on protecting the core asset that is at risk – the data. Similarly, most of the cyber-security spend is on perimeter security (and of course, premier security is still necessary) but comparatively little is spent specifically on data security per se.
There are a number of reasons for this. It’s partly because it takes time to effect change in any large organisation – it takes time for an effect to be felt, and then the organisation to decide to change, and then to execute that change. Also, and in general, security staff are rarely information experts that understand data – they are much more likely to have an intelligence services or military background where physical and perimeter security are paramount even today.
The source of the threats has also changed. Initially, threats always came from outside the organisation, but today threats are just as likely to come from within the organisation. Employees and sub-contract staff are clearly a risk – including as a result or coercion from external sources – e.g. serious crime and foreign states. This threat is increased where the employees hold privileged roles in IT such as system administrators and database administrators. Even the best perimeter and system security is unlikely to protect from data theft by a rogue DBA.
Whatever the reason, it’s worth putting some thought into the models we use for data security and re-validate them for the new threats. In fact we need to go back to basics and address the three basics of data security – CIA – Confidentiality, Integrity and Availability.
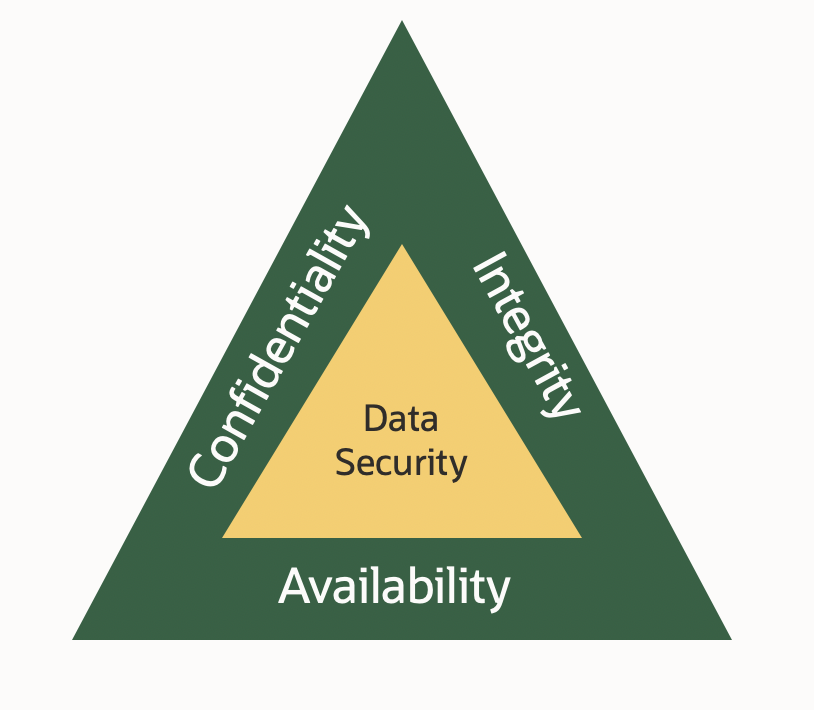
For Confidentiality we need to accept that least-privilege really is necessary for any security sensitive data – i.e. customer sensitive, commercially sensitive or high value data. This needs to extend restrictions to DBAs – they should not need to have access to data to do their day-to-day job (there are tools out there to achieve this today on most enterprise class databases) and good Separation of Duties controls should be in place for critical tasks.
Integrity asks that all database systems with sensitive data should be secure in themselves, and especially from internal threats or corruption. Servers and database binaries much be up to date with all necessary security patches, and those patches should be implemented as soon as they are available. All data should be encrypted at rest and in transit – especially important are database backups which are often forgotten. SQL insertion protection must be in place for attacks originating inside the organisation – perimeter web access firewalls are insufficient.
These protections should also be in place for any systems that hold “production” data – including test systems if they contain live data – again a typical weak area.
While nothing here is new, what is new to many organisations is the increasingly realisation that specific data security is no longer an optional capability – it is just as critical to prevent data breaches as the other security layers.
